Table of Contents
- Innovations in Stresser Technology
- Grabify Tools and Their Impact
- IP Spoofing and Layer 4 Attacks
- IP Stresser Use Cases
- Amplification Methods in Stresser Services
- Understanding DDoS Attacks
Innovations in Stresser Technology

Innovative stressers utilize machine learning and
automation to enhance load testing precision and uncover hidden vulnerabilities.
Grabify Tools and Their Impact

Using Grabify tools, businesses can detect and log malicious traffic,
enhancing their security protocols against targeted attacks.
IP Spoofing and Layer 4 Attacks
By adding a layer of anonymity through IP spoofing, stress tests can operate without
revealing the source, ensuring data remains confidential while assessing network resilience.
IP Stresser Use Cases

IP stressers are invaluable for organizations aiming to simulate high-traffic scenarios.
These tools highlight system vulnerabilities, helping businesses implement effective safeguards.
Amplification Methods in Stresser Services

CLDAP, DNS, and NTP techniques amplify network requests, generating an overload
that tests system capacity limits. These methods increase traffic impact significantly, often resulting in substantial strain on systems.
- DNS reflection method
- NTP boost method
- CLDAP traffic magnification
Understanding DDoS Attacks
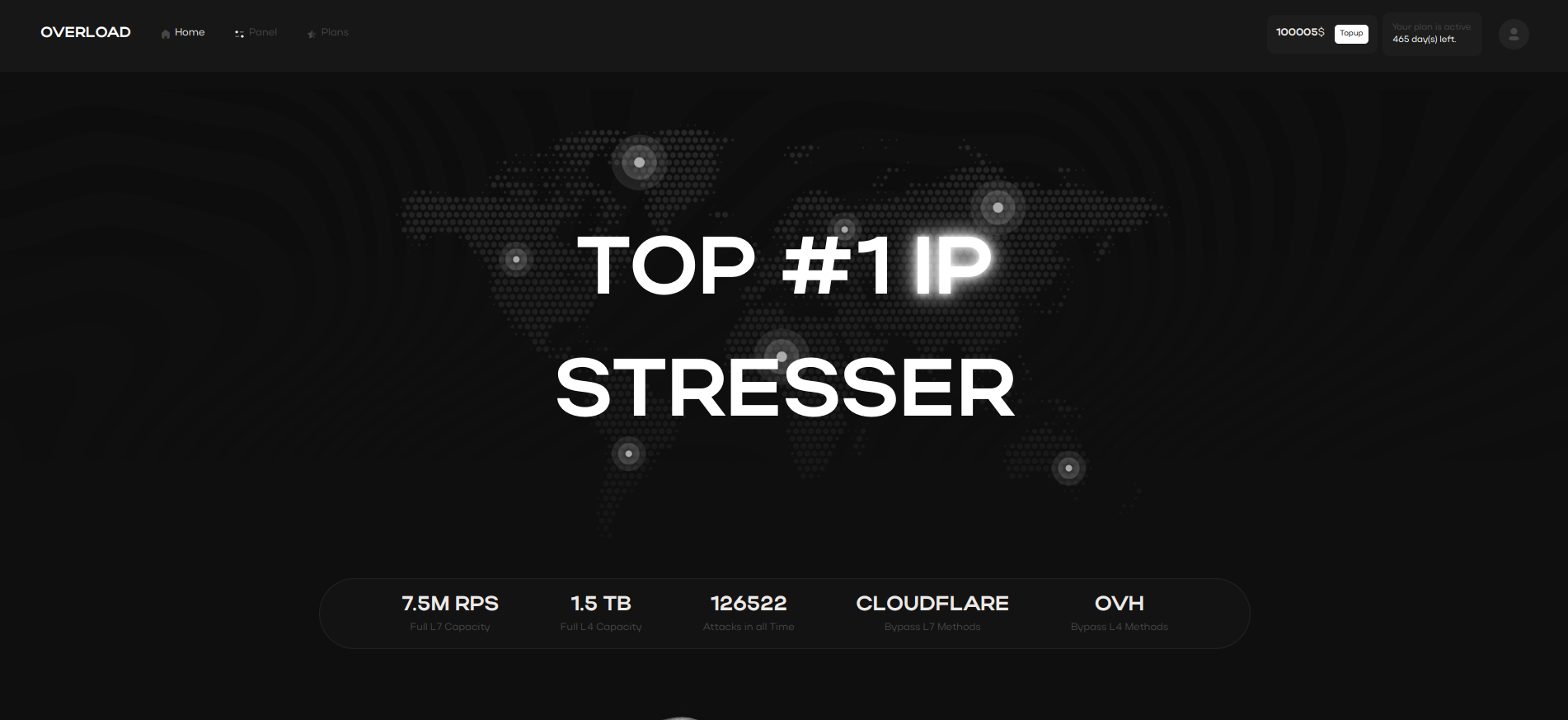
DDoS attacks are a significant threat to online operations, causing service disruptions
and financial losses. Understanding their mechanisms can help businesses mitigate risks and strengthen security protocols.